CTI Butler
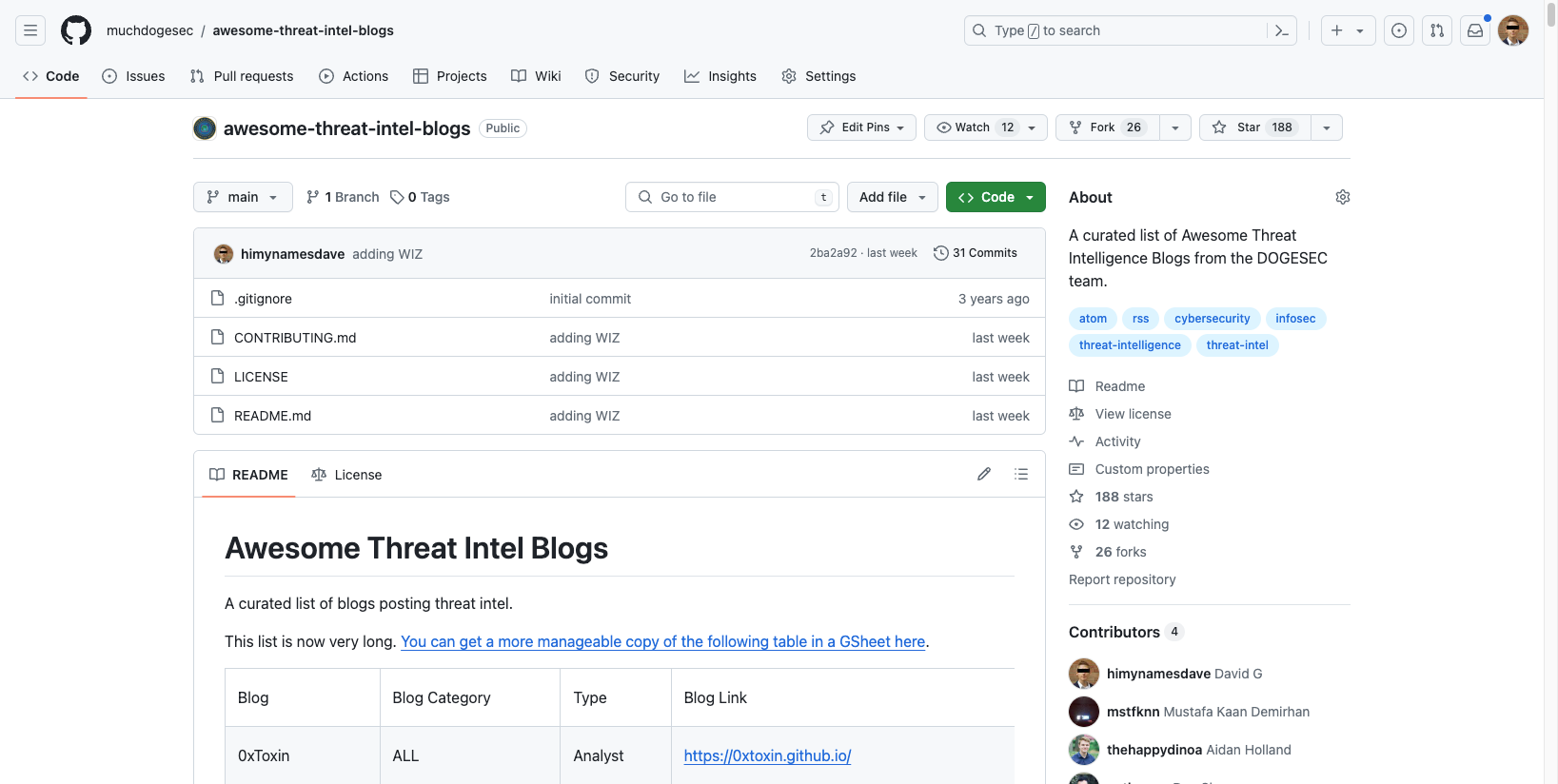
The most important cyber threat intelligence knowledgebases.
The most important cyber threat intelligence knowledgebases.
Know when software you use is being exploited.
Turn any blog into structured threat intelligence.
Your automated threat intelligence analyst.
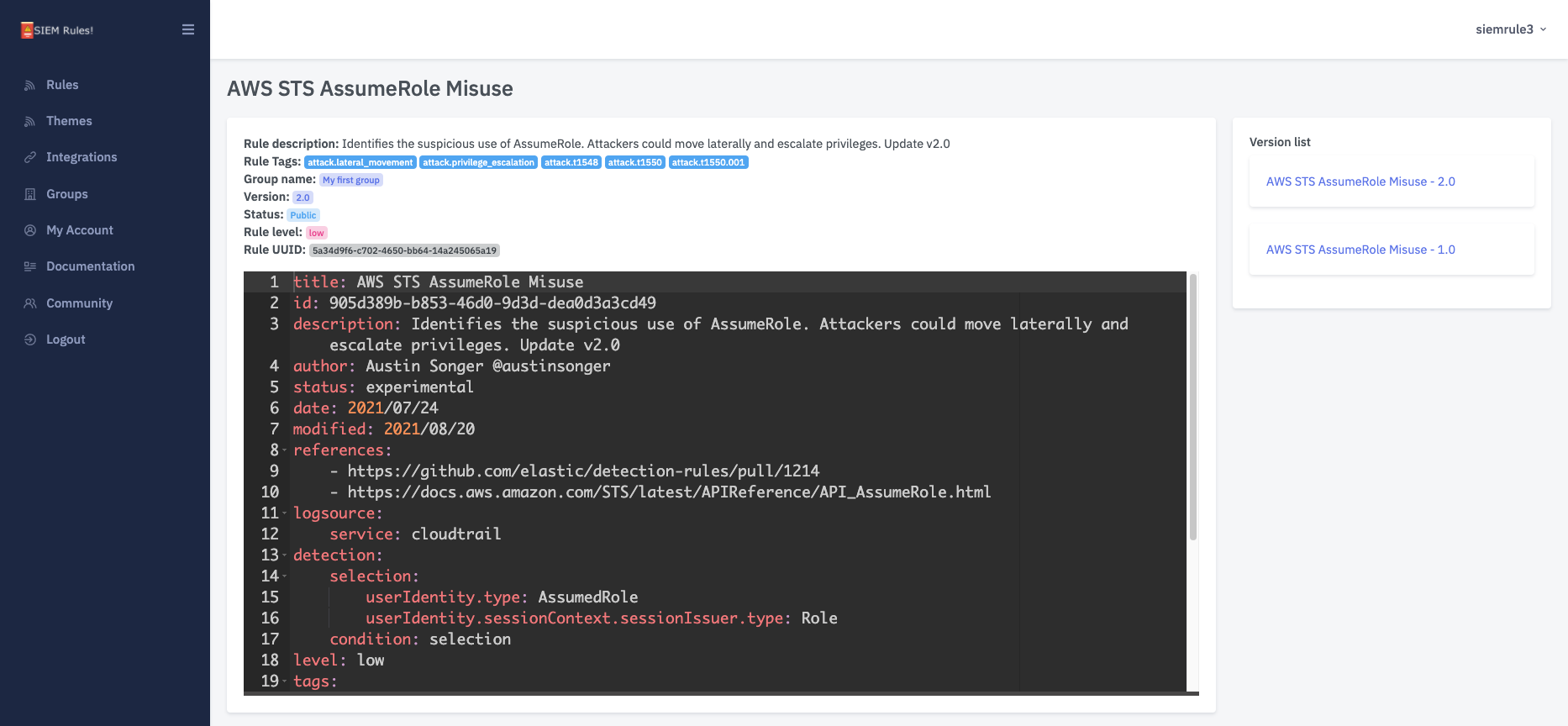
Your detection engineering AI assistant. Turn cyber threat intelligence research into highly-tuned detection rules.
The Market Place for Cyber Threat Intelligence.
All dogesec commercial products are built in-part from code-bases we have made available under permissive licenses.