Blog
The dogesec blog
-
A Producers Guide to Sharing Cyber Threat Intelligence
PRODUCTS March 03, 2025
txt2stix + stix2arango + arango_taxii_server = a robust and flexible setup for storing and distributing the cyber threat intelligence you've produced. -

Supercharging txt2stix with AI
PRODUCTS February 17, 2025
If you're a cyber threat intelligence analyst you probably use txt2stix, but have you seen some of the latest AI related features? -
Beyond the ATT&CK Matrix: How to Build Dynamic Attack Flows with STIX
TUTORIAL February 03, 2025
MITRE ATT&CK techniques are useful, but they don’t capture the sequence of an attack. Enter Attack Flows. -
A MITRE ATT&CK Style Knowledge Base for Ransomware
PRODUCTS August 19, 2024
After becoming ever-more frustrated by intelligence producers naming the same ransomware slightly differently, and with ATT&CK missing lots of ransomware types, I finally got around to trying to solve the problem. -
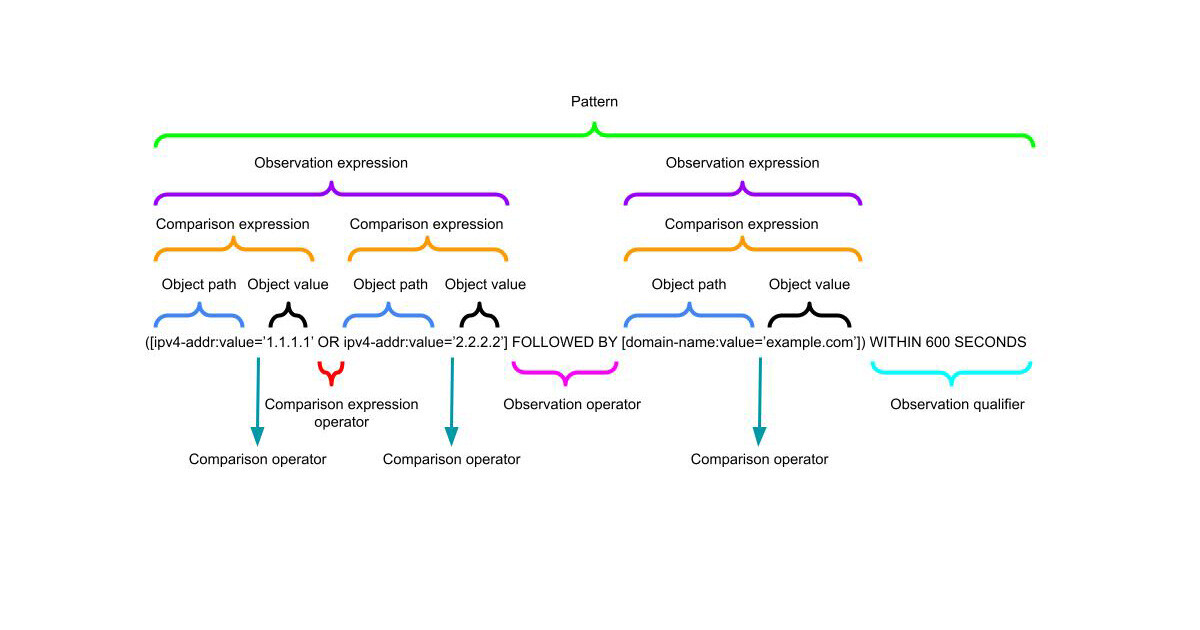
Constructing STIX Indicator Patterns to Write Detection Rules
TUTORIAL July 01, 2024
The STIX 2.1 Indicator SDO specification is flexible enough to allow for a range of detection languages. In this post I will show you how to use the STIX pattern language to write detections using cyber threat intelligence data. -
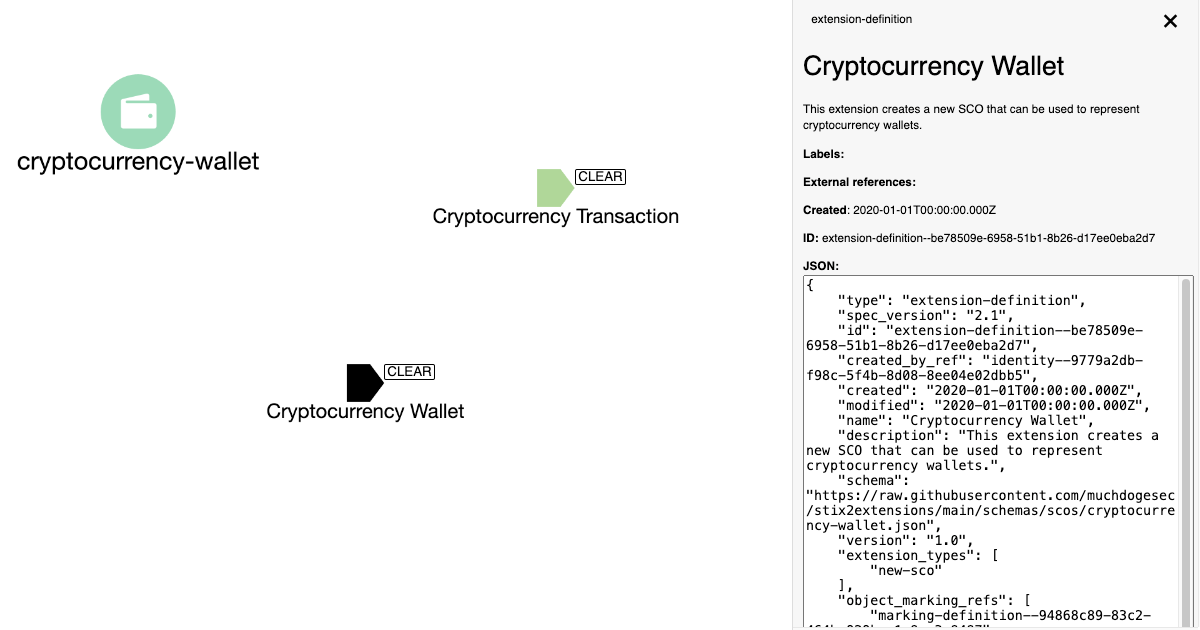
Creating Custom STIX Objects for Cyber Threat Intelligence
TUTORIAL June 24, 2024
Sometimes the default STIX 2.1 objects will not be broad enough for your needs. This post describes how you can extend the STIX specification when required. -
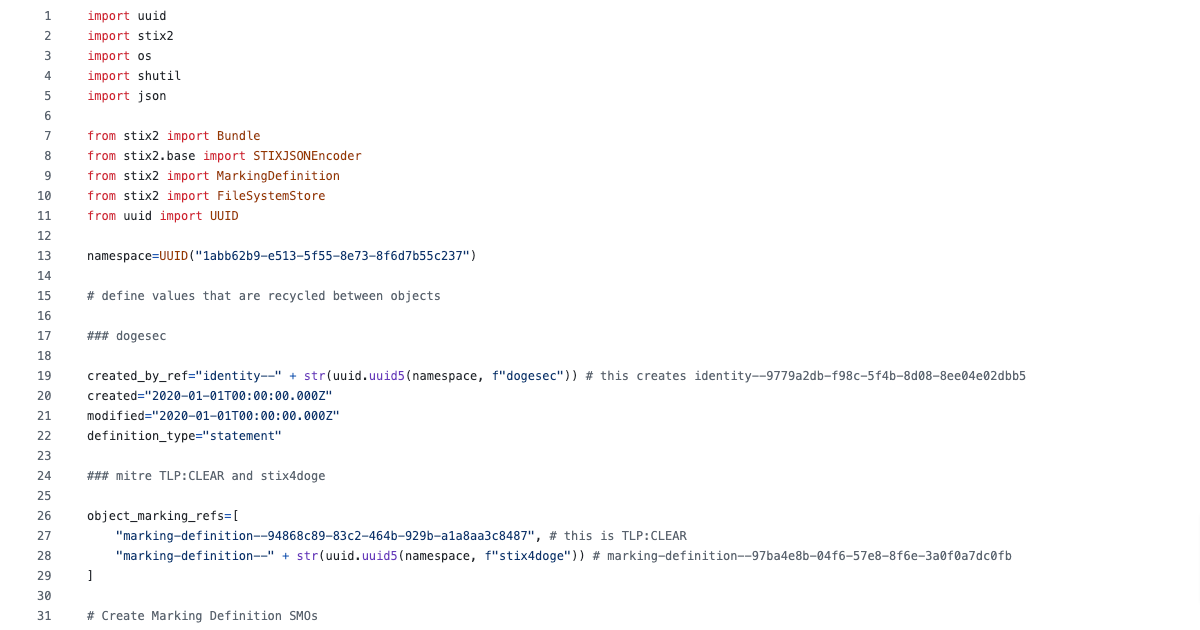
A Quick Start Guide to Generate STIX 2.1 Structured Threat Intelligence using Python
TUTORIAL June 17, 2024
A post full of code examples that will give you everything you need to start creating STIX objects to make it simple to share your threat research. -
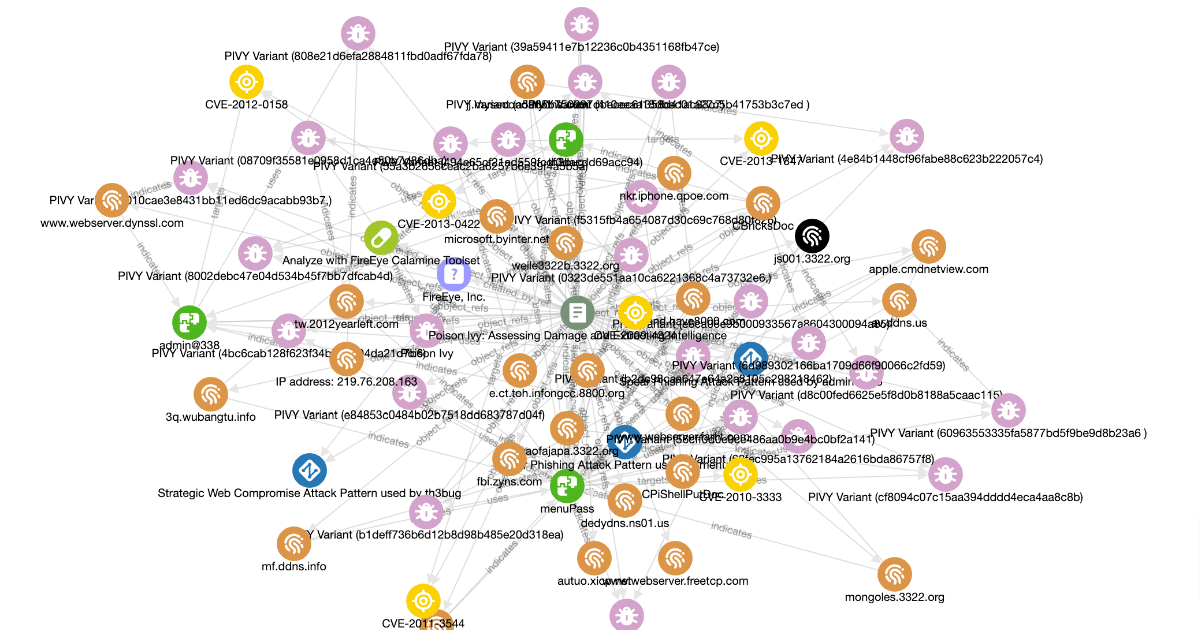
A Beginners Guide to Creating Threat Intelligence using STIX 2.1 Objects
TUTORIAL June 10, 2024
STIX 2.1 allows you to tell stories by connecting objects together to form the story-line of cyber actors, campaigns, incidents, and much more. In this post I explain how.